Wednesday, December 31, 2008
Cara Pasang Musik Pada Blog
* Masukan judul lagu yang anda inginkan pada search engine yang tersedia. Contoh : umbrella. Atau menuliskan nama penyanyi atau grup bandnya. Contoh Rihana
* Jika judul lagu belum muncul, biasanya ada tulisan Click here to get more Result. klik aja tulisan tersebut
* Setelah terlihat beberapa judul lagu, klik pada judul lagu yang sedang kamu cari, secara otomatis akan ditampilkan kontrol navigasi dan lagu yang dipilih tadi akan di perdengarkan
* Di pojok kiri bagian bawah ada kotak yang sudah di beri tanda centang, yaitu AutoStart, Show song Title. AutoStart artinya ketika pengunjung mengunjungi blog kamu, maka lagu akan langsung play. Nah jika tidak mau langsung play alias memberi kesempatan kepada pengunjung untuk memilih sendiri apakah mau mendengarkan lagu atau tidak, kamu hilangkan tanda centang tadi dengan cara mengkliknya
* Show Song Title artinya pada panel navigasi akan di munculkan judul lagu yang di muat. Jika tidak mau muncul ya hilangkan saja tanda centangnya
* Copy seluruh kode HTML yang di sediakan pada text area, paste pada notepad. Silahkan close window situs tersebut
* Langkah selanjutnya yaitu sobat tinggal masukan kode HTML yang diberikan tadi ke dalam blog kamu. Situs serupa yang bisa kamu kunjungi : www.songhere.com
Sunday, December 28, 2008
Membuat Home Networking dengan Wi-Fi
1.AktifkanWi-FiAnda
Langkah pertama yang paling penting adalah mempersiapkan perangkat jaringan wireless Anda dan mengaktifkannya. Cara mengaktifkan fitur Wi-Fi pada setiap komputer cukup beragam. Ada yang harus menekan tombol khusus baru kemudian aktif. Ada juga yang cukup mengaktifkannya melalui layar Windows Anda. Untuk mengaktifkannya melalui layar monitor; buka Control Panel, Network Connection, pada icon Wireless Network Connection klik kanan dan pilih Enable. Setelah itu, klik kanan kembali dan pilih View Available Wireless Network. Jika pada layar ada sebuah koneksi wireless tersedia, Anda tinggal pilih kemudian tekan tombol Connect.
2.BuatJaringanWi-FiSendiri
Namun bila koneksi Wi-Fi belum tersedia, Anda memang harus membuatnya sendiri. Apalagi pada komputer pertama sekali yang akan digunakan untuk jaringan. Caranya cukup pergi ke Control Panel, pilih Network Connection. Kemudian pada halaman NetworkConnection pilih Wireless Network Connection. Klik kanan kemudian pilih Properties. Setelah itu, buka halaman Wireless Network. Pada halaman ini berikan tanda centang pada Use Windows to configure my wireless network settings. Kemudian tekan tombol Add di bagian Prefered Networks.
3.NamakanKoneksi
Langkah kedua adalah menamakan koneksi wireless yang akan Anda buat. Nama koneksi dapat terserah diberikan, pengetikan nama koneksi dilakukan dalam boks SSID. Jika Anda ingin memiliki password untuk jaringan ini, pada opsi The key is provided for me automatically hapus tanda centang. Kemudian pada drop down menu Network Authentication, pilih Open atau Shared untuk menggunakan network key WEP atau memilih WPA-None untuk memilih menggunakan network key WPA. WPA memang lebih baik, namun tidak semua perangkat mendukungnya. Kemudian masukkan kuncinya pada kolom Network key dan Confirm network key.
4.BerikanPasswordWEP
Bila Anda memilih untuk memberikan password atau key secara manual, maka pada layar selanjutnya Anda akan dipertanyakan password tersebut. Bila Anda menggunakan password WEP (Wired Equivalent Privacy) ada aturan penggunaannya, yaitu hanya diperbolehkan 5 atau 13 karakter untuk penulisan password yang hanya menggunakan 1 jenis karakter. Untuk dua jenis karakter (angka dan huruf) hanya diperbolehkan sebanyak 10 atau 26 karakter. Perlu diingat bahwa semakin panjang dan rumit password akan semakin baik.
5.BerikanPasswordWPA
Anda dapat juga memberikan password WPA (Wi-Fi Protected Access). Pada penggunaan password WPA aturan yang harus ditaati adalah jumlah karakter yang dapat digunakan antara 8 sampai 63 untuk satu jenis karakter dan 64 karakter untuk lebih dari satu jenis karakter. Setelah selesai nanti, Anda dapat mencetak password ini untuk kemudian digunakan menambah komputer ke dalam jaringan nantinya. Dan perlu diingatkan bahwa penggunaan kunci WPA tidak selalu dapat diterapkan di setiap komputer. Ada beberapa perangkat jaringan nirkabel yang tidak dapat menerima kunci WPA.
6.AdHoc
Satu lagi yang perlu dilakukan adalah menjadikannya jaringan Ad Hoc. Jaringan Ad Hoc adalah jaringan yang hanya menghubungkan komputer ke komputer tanpa melalui sebuah hub atau router sebagai access point. Untuk jaringan nirkabel rumahan atau kantor kecil cukup menggunakan jaringan jenis ini. Oleh sebab itu, salah satu yang tidak boleh dilewatkan adalah memberikan tanda centang pada opsi This is a computer-to-computer (ad-hoc) network, wireless access points are not used. Opsi ini terletak di bagian paling bawah layar Association. Setelah selesai tekan OK.
7.MulaiBuatJaringanBaru
Langkah selajutnya adalah membuat jaringan baru menggunakan koneksi yang sudah ada. Langkah pertama dalam membuat jaringan Anda cukup mengikuti wizard yang ada untuk membuat jaringan biasa. caranya masuk ke Control Panel. Kemudian pilih Network Setup Wizard. Ikuti petunjuk yang diberikan. Pada saat wizard mulai dijalankan, Anda akan diminta untuk memeriksa kembali perangkat jaringan yang akan digunakan. Apakah sudah lengkap atau belum. Jika sudah lengkap Anda dapat melanjutkan. Jika belum pastikan terlebih dahulu semua perangkat sudah terpasang dan terinstal dengan baik.
Sunday, December 21, 2008
New tips from 1 hp
To get started you must first have an email to any email .. like yahoo or google .. I can also
But if I have a smell, please enter this address in your hp www.friendster.com
. So I enter and select the sign .. later given a form asking to optional fully completed .. yes ..
When I completed the list of email lu lu open later .. there are pointing the email from all .. But there are pointing to the email confirmation .. well Sign smell confirmation link ... I finish ..
I live to eat and then set the profile of reasons lu lu liatlah ... and I have my own .. well to facilitate the url TV, you can replace it .. you wish you .. url you will be
www.friendster.com / xxxxx
But I lu can okey wrong fsan hp through the past .. look forward to the next article.
Domain and hosting free
But later lu can have the opportunity to make menangin hosting and domain free of javahostindo
safe to try.
Trackback install tips on other blogs
1. Specify the blog that will make our target Trackback .. but that could just my idea .. .. I
2. We determined that there is a posting on the blog that you would like us Trackback ..
3. Give us a link in the posting that led to the blog posting x ..
4. Enter the posting down to us that there is an attachment .. But we enter the url x blog posting last .. we can know Trackback URL of the blog postings x .. but it's there we brati Sign url and I will be the end of the url / Trackback ..
Trackback profit from the content of some of the postings before we can comment column appears in the blog x .. But if there is a reading and interested visitors then so be it .. I smell ..
This article can be disseminated origin do not forget Logical link here with the anchor starwrite .. thank you ..
Download the free mp3
may be the most popular band at this time. Now here lu can download for free mp3 hp, for hitsnya story and merindukanmu Haha.
I downloaded the songs live here
and for D'MASIVER you can download disinisemuanya can be obtained free of charge but only through hp bulldozer safe play jolly .. ..
SEO Training contest for beginners
So I take it and go to 5 that could soon rise .. .. all of us can only support the bloggers in the Busby SEO test .. we have the newcomer also struggled in the contest with SEO beginners keyword "SEO training for beginners"
Tips to read the email through hp
The advantage to read the email through hp is we can save cost and easy wherever ..
Tools needed:
1. Hp that can access the Internet, here I am using hp nokia 6070.
2. And the balance of your card number sparingly in accessing the Internet, here I use the card as and Mm3.
Now you are ready to read the email. I want you how.
Next steps to be followed.
Start by writing dibrowser you www.yahoo.com
continue to eat directly into the email option will be asked yahoo id and password we have.
So now you can read the email through your hp ..
If you still can not read the email through hp you please comment here ..
Computer magazine

Over the past decade, Computer has published numerous articles on NASA’s pioneering efforts in robotics, artificial intelligence, and software engineering. In honor of the celebration of its 50 years of achievement, in this issue we have assembled articles describing some of NASA’s contributions to the field of computer science. Other articles in this issue describe efforts to extend Amdahl’s law to account for power scalability’s implications in the coming many-core era and detail the development of a model that uses genetic algorithms to optimize the assignment of private transport within a city area.
Saturday, December 20, 2008
Blogger Vs West World Blogger Indonesia
First, have a website or blog just hobbies or just a web Presence, not be treated as a business that generates money. Blog or website in order to become this same case with mobile phones, ipod or other gadgets that follow the social trend.
Second, most of us are not accustomed to reveal the thoughts and feelings in writing. Our culture is a culture of personality oral alias. Even in the formal education system we should not write things that dibiasakan. So, writing is a difficult material.
Third, the mastery of the English language is not adequate. Blogs / websites with content, language readers will be limited only netter and people outside who understand the language. This is not as profitable adsense publisher. Moreover, Google AdSense not support the Indonesian language. Required content in English or other foreign languages supported by Google AdSense to generate income. If in the Indonesian language course we are still difficult to write, let alone in English or foreign languages.
Fourth, mental laziness and instant. We want to generate quick dollars from Adsense, while we are not accustomed to write, especially in the English language. But that happens is to take content from other sources by way of copy and paste copy. The most important blog / website filled and update. This is the easy way. This is related to the above factors, first, because we do not memperlakukannya business as we consider the lack of originality, inattentive the principles of web design, search engine optimization (SEO), keyword research (keyword research), the format and layout of adsense, etc..
Fifth, the sense satisfied with the results obtained small. Enough Cent few dollars per day, we make it to "all workers" are satisfied with recehan and crumb from the "big bread" provided by Google AdSense or other Affiliates. $ 1 a day can only work with copy and paste the copy as a sizable additional salary of office, or extra pocket money for students and the students.
Perhaps there are still other things that cause the habit copy and paste copy of this, but in the top five, I think that is enough to describe the real situation. Nevertheless, the changes will always occur. Already there are some people that seriously want to become a professional adsense publishers. Or they are seriously incomenya rely on sources from the internet. Acquisition of up to hundreds of thousands of dollars per month from Google AdSense is the more often we hear of Indonesian bloggers. So, do not worry, they will get serious results are satisfactory, and it will spread like a virus. We see it later ...
Writing a Book
When I opened the book the first time, I feel surprised and at the same time so honored to know that it’s my forword that has been trusted to appear in its entirety in her book. Just for the record it’s not only me who’ve been requested by Jennie to make introductory remark. I think it’s her unique way to remind me that “here’s your foreword in my book, let me give my forword in your book” kind of thing. In other word, time is rife for me to write a book. Yet I still have an accuse to myself: I’ll start it when I were at home in a few months time. Hopefully, I won’t find another accuse once I get there.
In any case, thanks a lot to Jennie S. Bev for your trust in me. And for everyone who wants to buy the book, it’s available now in bookstand in your nearest place all over Indonesia. On the content of the book itself, if my friends response –all of them read it in a day– are to be used as barometer, I’d predict it’ll be a best-seller book as far as it’s got good support from the distribution front.
Writing a book is a standard “value” of being “expert.” Anyone should refuse to be called expert unless he/she writes a book on the matter. Unfortunately, it’s not the case in Indonesia. In some cases, some the so-called expert actually never have any book or published article in some respected international publication.
Update:
I forget to tell that so far I’ve received three offers from publishers to write a book, one in English and the other two in Bahasa Indonesia. I hope I can keep my promise to them sooner rather than later.
How to Write Email Selling?
How do I actually write an email to sell? Next I tried to give this description. 1. Making the title to attract the attention of the email. The title of the email is very important in email marketing. The title is the same email with a news headline in the newspaper if it. That is, make the title of your email attract the attention of the recipient to open your email. Make the recipient of your email to be curious with the email you send. The title is essentially an email and priority Important! If you fail to do this ... I do not expect a lot of your email will be opened. What is important is do not lie to the email, what should be written dijudul related to the content of the email. Because email marketing is built on the basis of trust and relationship-oriented long-term friendship, especially with kastemer and prospective kastemer you. In writing the title by avoiding megawali title with a bunch of stars (*), excitement (!), Question (?), Dollars ($) and other simbul simbul. Usually the title as this will directly didelet by the recipient, as indicated spam ... this habit that I do:) I also do not use email that is not clear, for example: scdjyghg@webanda.com ... I usually also direct mendelet email like this, you may also? 2. Personalkan your email to each individual (the name of the recipient). Try to mention the name of the recipient email in your email. Full name or the call is also not a problem. Because with his name, the recipient will be more familiar taste and feel personalitasnya. For example: Yanto are? Yanto or hallo? or O Yanto ... how do you? 3. Remind them who you are, and you get from contact with them. If you send an email to someone first, or do not have long contact them immediately remind them who you are and where you know their email in a row beginning your email. For example, "I Budi www.BengkelMotor.com motor workshop owner, I get a contact email as you fill in the fields our newsletter some time ago." Fill follow the next steps .... 4. Disclose profit for the recipient on the line or the first paragraph. In email marketing, earned benefit or advantage if someone receives an email from you. And profits / benefits that they receive in writing the first paragraph. For example: "As acknowledgments have visited our website, please come to our workshop to get the service free only to bring print out this email." <-This time for first contact. If that is kastemer or send candidates kastemer long, can be like this: Mr. Yanto, you will get a 50% discount fee service with only print out this email. Pak Yanto but remember this is only valid for this month too. 5. Write a short email and to the point of it. Please email with short and to the point only. Usually people would be so lazy to read if he is to see the email is too long. Including you, is not it? Get the time from the recipient to read the entire email you. better email you have finished reading within 30 seconds to 1 minute. 6. Tell your readers (the recipient) how to contact you, especially to order goods that you sell. I also do not forget to include the address of the contact person how to contact you. It is important to avoid a potential candidate kastemer lost it. For example: "For more information please contact: Gandhi Motor Workshop Jl. jl.Magelang KM 5 Yogyakarta Phone. 0274-632987 Fax. 0274-632789 Welcome to try! About the author: Sugandhi is a business |
Terminal Black Blogger XML Theme
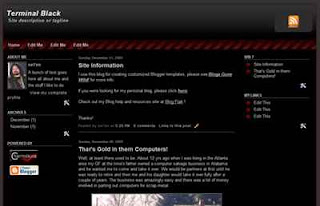
This theme is a 3 column design for Blogger XML with full support for drag and drop widgets in the sidebars and the footer area. It’s fixed width for a 1024 wide screen or wider. It features a built in RSS feed and an easy to edit horizontal navigation bar in the heading. You can easily add or remove links thru the Edit HTML editor. It’s a a sleek and uncluttered layout that will allow you to add lots of sub-sections in the sidebars.
This theme is virtually identical to the previous Terminal Display template except for the black body area background instead of dark grey.
Technical help for this template:
Installing the skin
Backing up your widgets contents
Tags: blogger, xml, blogs, themes, blogspot, templates, web design, free skins, adsense
Sandbox users with Windows 7 PC Safeguard

If you share your PC with many users, some of whom may be messy users with a habit of littering files and changing settings, or you might just be a privacy nut who doesn’t like to leave any traces behind, either way, a new and previously unannounced feature in Windows 7 called “PC Safeguard” might just be what you’re after.
First noticed by the enthusiasts at JCXP.net, “PC Safeguard”, as it is called in the Windows 7 user account settings, prevents specified standard user accounts (cannot be applied to admin accounts) from making permanent and unwanted changes by removing all changes and files saved after the user logs off.
Credit where credit is due, this feature is not fundamentally new. Since 2005, Microsoft has offered a tool previously known as the “Shared Computer Toolkit” now “Windows SteadyState” to both Windows XP and Vista users to do exactly this function and a little more. The interesting thing however is that the feature is now baked into Windows 7 - making it more widely known to users as well as simplifying the process drastically.
To enable this feature, click on the “Set up PC Safeguard” link when managing a user account. Select the “Turn on PC Safeguard” option, apply and wait approximately 5 minutes whilst it ponders about the question of life. It might seem like it’s not responding, but trust me, the magic is happening.
If you’re big brother with a soft spot, you can also tweak the Safeguard feature to allow users to access individual hard drive volumes. One scenario where this might be useful is to set up a small 1GB partition where the user can secure their files without resorting to removable media.
Now when that user logs on, they are presented with this message window reminding them their files will be removed after log off. Also when they try to add files to their user folders, a popup appears, reminding the impending vaporization.
From this point on, the user experience is identical to any other standard user’s. They can access applications installed for all-users, change wallpapers and themes and download files. There’s no performance impact, nor additional restrictions. The difference however is that everything will be reverted to a blank state the next time they log in. Metaphorically speaking, it’s like IE8’s InPrivate or Google Chrome’s Incognito for user profiles.
I suspect this feature will be fined tuned in the coming Windows 7 builds to inherit some of the more advanced features of SteadyState (ex. time restriction and application blacklist) but I can already see this very popular with home and public computers.


